Fraud Education
Recent Scams

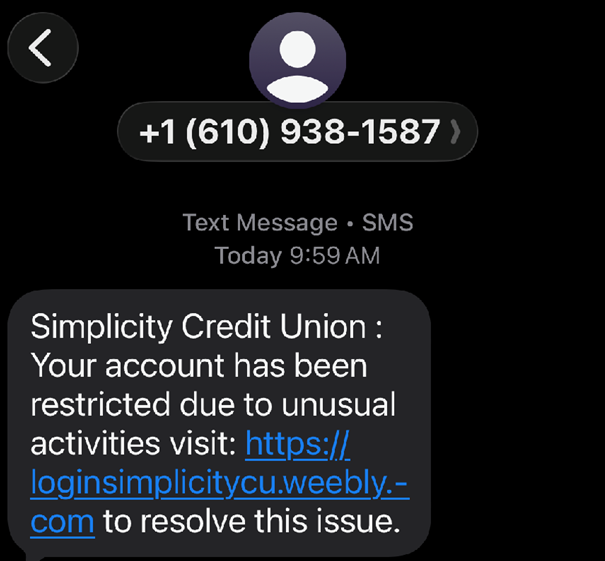
Text Smishing Fraud: 01/12/2026
We have received reports of fraudulent text messages circulating in our area that are not from Simplicity Credit Union.
These scam texts claim your account has been restricted due to unusual activity and prompt you to click a link to resolve the issue. The link leads to a fake version of our online banking login page designed to capture your username and password.
Our security partners have identified and shut down one of these fake websites, but the scammers have since created a new spoofed page.
If you see this message, don't interact with it. Delete it and report it as junk if possible.
If you believe you may have clicked a link or shared your information, please contact Simplicity Credit Union immediately so our Fraud Department can assist you: 844.769.2667
Please remember:
- Simplicity Credit Union will never ask you to click a link or provide sensitive information through a text message.
- Be cautious of any unexpected texts that include links or urgent requests.
- If you’re unsure whether a message is legitimate, contact us directly using a phone number you know and trust.
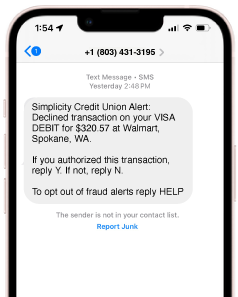
Text Smishing Fraud: 06/25/2025
Our team has been notified that members in the area have been getting fraudulent texts asking them to verify a charge. The text asks them to reply 'yes' or 'no' if this was their transaction.When they reply, a bad actor calls our member impersonating Simplicity and spoofing our phone number. The member is asked to verify pieces of their card information like a portion of their card number and PIN. Since our debit cards all start with the same six digits, they are able to get the full card numbers. From there, the bad actors are putting through large Pick 'n Save transactions at locations around Wisconsin. This is a smishing scam and NOT a legit notification from Simplicity CU.
REMINDER: We will never ask for more than the last 4 digits of their card number to identify it and we will never ask for your PIN.
If you see this message, don't interact with it. Delete it and report it as junk if possible.
If you have already received that message and provided your online banking information, contact us right away: 844.769.2667
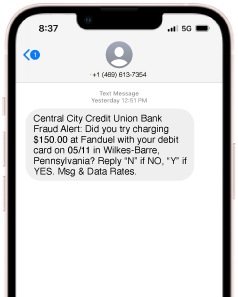
Text Smishing Fraud: 05/14/2025
Our team has been notified that members in the area have been getting fraudulent texts asking them to verify a charge. The text asks them to reply 'yes' or 'no' if this was their transaction. When they reply 'no' a bad actor calls our member impersonating Simplicity and asks them to verify the last 10 digits of your card number. From there, the bad actors are putting through large PayPal transactions on the card and are coaching members to confirm the transaction as legitimate when our real Fraud System reaches out to verify it. This is a smishing scam and NOT a legit notification from Simplicity CU.
If you see this message, don't interact with it. Delete it and report it as junk if possible.
If you have already received that message and provided your online banking information, contact us right away: 844.769.2667
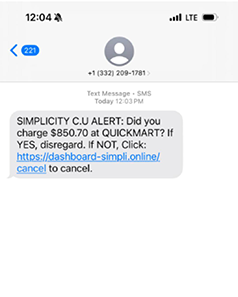
Text Smishing Fraud: 03/15/2025
Our team has been notified that members and non-members in the area have been getting fraudulent texts. This is a smishing scam and NOT a legit notification from Simplicity CU.
If you see this message, don't interact with it. Delete it and report it as junk if possible.
If you have already received that message and provided your online banking information, contact us right away: 844.769.2667
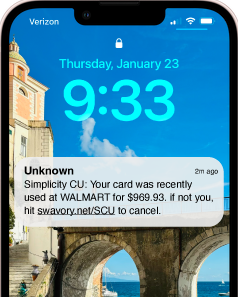
Text Smishing Fraud: 01/23/2025
Some Simplicity member have reported getting a text claiming their account was used for a large transaction that prompts them to click a link to cancel if it wasn't them. Once they click the link they are told to enter their OLB login information for verification.
We want to remind you that is is a common fraud tactic and Simplicity would never ask for your login information. If you see this message, don't interact with it. Delete it and report it as junk if possible.
If you have already received that message and provided your online banking information, contact us right away: 844.769.2667
Update: 01/29/2025
We have heard that the texts are claiming they're for Walmart & JC Penney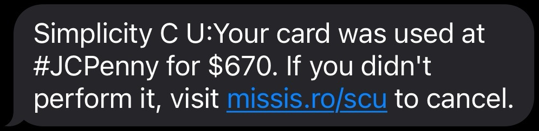
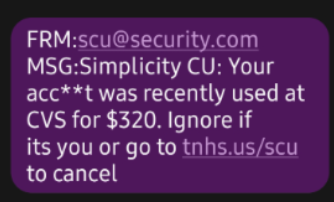
Text Smishing Fraud: 11/07/2024
The Simplicity Team has gotten reports of a new scam in the area involving fraudulent texts.
In the cases we’ve seen, members receive a text notification appearing to be from our fraud department asking them to verify a recent (fake) transaction. The member is prompted to follow a link to "cancel" the transaction if they don't recognize it. When the member clicks the link they are asked to log into their online banking which could give the fraudsters access to a member's funds and account information.
The first warning sign that might be helpful for you to avoid this scam is that it asks you to provide your online banking login information. We will never ask for your username or password and you should never share that information.
If you’ve already received this text and provided your info, we can still help. Contact our Fraud Department immediately: 844.769.2667
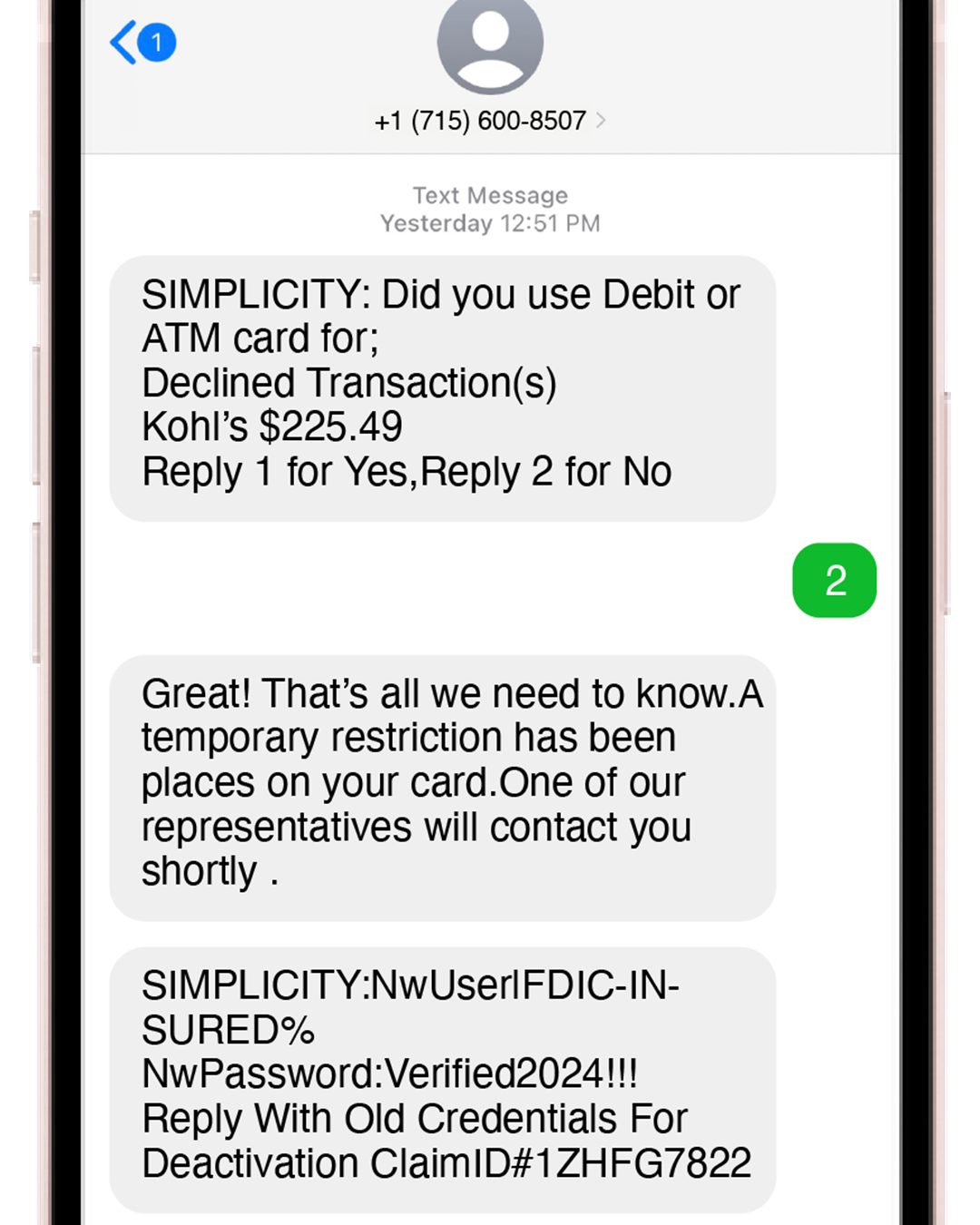
Text Smishing Fraud: 04/24/2024
The Simplicity Team has gotten reports of a new scam in the area involving a dangerous combination of fraudulent texts, phone calls, and online banking takeovers.
In the cases we’ve seen, members receive a text notification appearing to be from our fraud department asking them to verify a recent (fake) transaction. When the member replies “2” to the text, the fraudsters call from what appears to be our phone number and ask for their debit or credit card details and other personal information that could help them takeover their cards or online banking accounts.
The first warning sign that might be helpful for you to avoid this scam is that the fraud notification is coming from the phone number 1-715-600-8507 instead of one of the short code number that our fraud team uses.
If this sounds familiar, it's because we had the a similar scam going on earlier this year.
If you’ve already received this call or text and provided your info, we can still help. Contact our Fraud Department immediately: 844.769.2667.
IMPORTANT
If someone is asking you to provide ANY personal or online banking information; specifically username, password, and the secure access code that gets sent when logging into online banking on a device that’s not registered, DO NOT give them that information. If a fraudster has access to that secure access code, that gives them the ability to get into your online banking information where account numbers can then be compromised and fraudulent activity can happen from there. Money can be depleted in and out of those accounts very quickly, especially in the event of depositing fraud checks via mobile remote deposit capture (RDC) where P2P payments, or external transfers are authorized by the fraudulent person.

Never provide your confidential banking or personal information to anyone other than a reputable merchant you trust. If you do, you risk being held responsible for any potential losses. If something does not seem legitimate, it probably isn't!
Always just delete texts, emails, or hang up on scammers. Call the merchant they claimed to be or call us with help on whether a scam or not.
Online Security and Avoiding Fraud
Don’t be a victim!
There are many types of fraud that are constantly evolving year after year. However, the majority usually have several things in common: a victim’s good nature, a victim’s lack of banking/financial knowledge, and/or a victim’s poor financial situation. More often the victims are very young or elderly.
Simplicity staff members stay alert for fraud and are constantly defending against it. However, not all cases can be prevented without the help and awareness of our member-owners. By working together, and identifying key components that trigger suspicion, we can pursue investigation early and partner with local and national anti-fraud efforts.
Staying ahead of the curve and being aware of the more common scams is the best way to avoid fraud. Most ongoing scams have similar traits, and they become easier to identify. Another thing to remember is that strangers don't give away money. Again, if it seems too good to be true... it probably is.
If you believe you have fallen victim to any type of fraud relating to your account(s), please call us at 844.769.2667 as soon as possible.
Learn more about protecting yourself against fraud at the Federal Trade Commission.
Common Scams
You’ve probably heard the phrase, “Imitation is the sincerest form of flattery,” but when it comes to impersonating websites, this couldn’t be further from the truth.
Phony websites may look like a real version of a website, but in fact, they may be a resource for gathering account information or credit and debit card numbers. They are often tied to fake social media sites, emails, limited-time offers, and ‘unbeatable’ deals.
Keep your accounts safe by paying close attention to web addresses to be sure you’re on your intended website. Watch for spelling errors and double-check that the customer service number is correct.
- Do not simply trust the look of an email: question the intent of the email. Is it ultimately asking you to verify or enter personal information?
- Before clicking on anything, check the email address of who sent it. If it doesn't look normal (name@company.com), it is likely spam or fraudulent.
- If you receive a suspicious email with a link from a known contact, confirm the email address is legitimate by calling or emailing the contact; do not reply directly to a suspicious email.
- Check for misspellings, poor grammar, or incorrect domains within any links (e.g., if an address that should end in “.gov” ends in “.com” instead).
- Do not trust a website just because it has a lock icon or “https” in the browser address bar. Always carefully check the URL to be sure that you’re on the right website.
Be aware of an internet email fraud form known as phishing. This practice refers to fraudulent email messages requesting confidential information. The information then allows the perpetrator to gain access to the victim's accounts and steal the victim's identity. This may include
Emails asking you to reset account information, restore access or for confidential information
Suspicious, unsolicited emails containing attachments or requiring members to send personal information to us via email or pop-up windows
Maintenance/Account Recovery emails
Please remember that Simplicity will never ask for personal or account information by email. However, if you do receive one of these types of emails above,
- Do not respond to the email in any way
- Do not click any links
- Do not open any attachments
- Do not provide any data to any websites
Below are the five common types of phishing attacks according to Meta Compliance.
Spear-Phishing: This type of targeted attack focuses more on stealing sensitive data from an individual or specific organization. Personal information that is specific to the target individual or company is used to seem more legitimate.
Vishing: This type of attack refers to “phishing scams that take place over the phone. It has the most human interaction of all the phishing attacks but follows the same pattern of deception. The fraudsters will often create a sense of urgency to convince a victim to divulge sensitive information.” These calls are usually made using a normal ID to make it appear safe to answer. For example, a hacker could pose as a representative at your bank or credit union and call to alert you that there has been questionable activity on your account. Once they’ve gained your trust, the hacker will ask for your personal account information and can use those details to commit identity fraud.
Whaling: This type of attack includes a high-level choice of target; it is an attempt to steal and misuse senior management’s private, personal information at a company/organization. Whaling occurs in the form of emails that are more sophisticated than phishing and are often harder to recognize due to their use of elite corporate language. The email will include personalized information about the target and organization.
Smishing: This type of attack is unique compared to its counterparts as it uses SMS text messages to gain access to personal information like credit card numbers, passwords, and more. The delivered text message usually includes a call to action to demand an immediate response or reaction.
Clone Phishing: The last type of attack involves “legitimate and previously delivered email [that] is used to create an identical email with malicious content. The cloned email will appear to come from the original sender but will be an updated version that contains malicious links or attachments.”
Reporting Fraudulent Activity
If you believe you are a victim of phishing, it is important that you change your password, monitor the activity in your account for a period of time and even contact credit reporting services to have a fraud alert attached to your credit report file.
Also, please notify Simplicity Member Call Center at 844.769.2667.
The most common check scams involve a person receiving a generous check instructing them to send cash or wire funds from the check proceeds to another person or company. What ends up happening is the check returns as a fraudulent check, and they are held responsible for the loss of the funds due to the return of the check. Below are common check scams that are seen on a daily basis.
Lottery Winner
The victim is mailed a check along with a letter stating they are the lucky lottery winner. The victim is then instructed to deposit the check and send a portion of the funds back to pay for the processing and taxes for the larger lottery winnings. The check that is attached to the letter will have been written off of a company or individual’s account that is in no way associated with the lottery.
Secret Shopper and Work-From-Home
Fraudsters create job postings or create a website advertising work from home jobs or to become a secret shopper to earn extra income. Often these sites advise the prospective victim to deposit a check and then to wire the majority of the money to a third party to purchase office equipment or to test the institution's customer service levels.
Overpayment
One of the trending internet check scams is found on sale sites such as Craigslist or eBay. The victim sells an item and receives a check for 2-5 times the agreed-upon sale price. The purchaser advises the Seller they wrote the check out for too much money by accident and for the Seller to send back the difference to them. Often the Purchaser will tell the Seller to keep the sales price of the item sold along with $50 for taking the time to wire the funds back to the Purchaser.
These types of scams typically involve connecting with the victim on social media sites or for online payday loan offers requesting the victim’s debit card and PIN number and/or the victim’s online banking username and password.
Debit Card Scams
The victim is contacted utilizing social media sites such as Facebook, Instagram, Twitter, etc. The fraudsters tell the victim that they need to use local bank accounts to conduct some business transactions and will leave some money in the victim's account for the use of their debit card and PIN number and/or online banking username and password.
Once the victim agrees, the fraudsters deposit fraudulent checks into the account via ATMs and/or remote deposit. The fraudsters then make ATM withdrawals and purchase Visa or GreenDot prepaid cards to convert into cash later. The victim is left responsible for the losses to the account due to their participation in the scam by giving their card and information to the fraudsters.
Payday Loan Schemes
The victims of this scheme are in need of a small loan to help make ends meet. The victim signs up with an online loan website and is quickly approved for a small loan with no questions asked. The fraudulent loan company will ask for the victim’s online username and password and states that they need the information in order to transfer funds to the victim’s account.
The fraudulent loan company then instructs the victim to send the money back to them to ensure the loan applicant (victim) is trustworthy. The fraudulent loan company actually deposited fraudulent checks into the victim’s accounts through the online banking application. The victim is left with a negative balance due to the checks deposited by the fraudulent loan company.
Resources
Equifax
Order Credit Report: 800.685.1111
Report Fraud: 800.525.6285
equifax.com
Federal Trade Commission
ID Theft Hotline: 877.IDTHEFT
consumer.gov/idtheft
ftc.gov
Experian
Order Credit Report: 888.397.3742
Report Fraud: 888.397.3742
experian.com
Identity Theft Resource Center
itrc@idtheftcenter.org
Contact: 888.400.5530
idtheftcenter.org
Trans Union
Order Credit Report: 800.888.4213
Report Fraud: 800.680.7289
tuc.com
Privacy Rights Clearinghouse
Contact: 619.298.3396
privacyrights.org
How You Can Protect Yourself
Simplicity CU knows the significance of protecting members' confidential personal and financial information. You should never disclose your private personal or financial information (e.g., Social Security number, account or card information, user IDs, and passwords) to anyone, either in person or over the phone, computer or mobile device, unless you know and trust the individual and you initiated the call or transaction.
Simplicity CU will never call and ask for your personal or financial information. If you receive a call, text, or email asking for this information, do not respond and notify us at 844.769.2667 immediately.
- If you are using Windows 7 or an older operating system, upgrade to a more current operating system, such as Windows 10. Microsoft is no longer providing product support, including security patches, for Windows 7.
- Use a firewall and install anti-virus, anti-spyware, and ad protection software on your device, and check for regular updates
- Never download software presented in pop-ups or emails from unknown senders
- Set your operating system, security and application software (such as Microsoft Office) to automatically check for updates
- Commit your user ID and password to memory. Do not record and store it in a place where someone can easily find it or use password memory/management programs.
- Do not use the same user ID and password on multiple sites
- Change your password frequently
- Always sign off Online Banking and Mobile App sessions
- Do not sign on to Online Banking from a public/shared computer
- Do not reply to suspicious emails, texts or voice messages on your computer, tablet, or phone
- Only use trusted third-party sites
- Safeguard your user ID and password. Sharing your online credentials with another individual, application, or company provides that party with the ability and authorization to access your accounts. Simplicity CU will not be liable for loss resulting from sharing your online credentials with a third-party except as applicable law requires.
- Monitor your accounts. You are generally not liable for online transactions you didn’t authorize that occur through the use of our online services. However, you should monitor your accounts and notify us as soon as possible when you detect unauthorized activity on any of your accounts. If you fail to notify us promptly, you may not get back all the money you lost. Please contact us at 844.769.2667 immediately if you notice any suspicious or fraudulent activity.
- Never share personal information by telephone, unless it is with a trusted entity with whom you initiated the call
- File documents that contain personal information in a safe place, and shred any unneeded documents containing personal information
- Pay attention to billing cycles, and contact creditors if bills do not arrive
- Review all financial statements regularly for fraudulent activity
- Review credit reports annually (free credit reports are available in your Online Banking through SaavyMoney's Credit Scores or at Annual Credit Report.com)
- Do not carry your Social Security card or excess credit cards on you unless absolutely necessary
- Remember to use caution when checking your email or searching for popular key words and videos online
- Be cautious when selling items online or on social media. Some scammers will pay for items by sending you fraudulent checks in amounts higher than the selling price and then requesting you to wire the difference back to them.
- Only use peer-to-peer (P2P) payments to send money to trusted family and friends – P2P payments are not reversible once sent
Peer-to-Peer Payments
Peer-to-peer payments, also known as P2P payments, are transactions that can be used for anything from splitting a $30 dinner bill between friends to paying your rent. These payment services allow the transfer of funds between two parties using their individual financial institution accounts or debit cards through an online or mobile app. Online services and apps that allow you to easily send and receive money are a fast-growing trend. Payment services, like Venmo, Zelle®, Apple Pay, Cash App, and Facebook P2P Payments in Messenger, are a virtual imitation of paying or receiving cash. These services make sending funds just as easy as paying with cash. However, you should only use these services when you are paying someone you know. Here are some tips to keep in mind.
Best Used Among Friends and Family
To lower the risk of being victimized by fraudsters, only conduct P2P transactions with people you know. Don’t use P2P payments to pay for items you purchase from unknown sellers on the Internet. Most peer-to-peer transactions are instantaneous and irreversible, a fact scammers are known to exploit.
Once you send funds, there is no recourse to get the funds back. If you accidently choose the wrong person in your contact list or enter the wrong number, the transaction cannot be stopped or reversed.
Don’t Use P2P Services for Business Purposes
P2P payment services are intended for personal use only. Most services have rules that prohibit their use for commercial purposes, such as the buying and selling of goods and services. Read the Terms and Conditions of your P2P service carefully, as some payments could be revoked, and your use of the service may be discontinued if you violate the provider’s terms.
Understand the Risks
Because P2P transactions are completed by a third party, the Credit Union does not have access to any information about these transactions even if they involve Credit Union accounts. In addition, P2P payment service providers are only responsible for transferring the funds. Once funds have been sent as authorized and received, they are no longer responsible for the transaction. If you paid for something but didn’t receive it or received damaged goods, you are usually on your own when it comes to a dispute. Before using a P2P service, research the provider’s customer support policies so you know what to expect. While these transactions are very convenient, you should view them as cash payments that can’t be retrieved.
What to Do if You Are a Victim of Identity Theft
- Contact one of the three major credit bureaus immediately to request a fraud alert, which places a notice on your credit report that you may have been the victim of fraud or identity theft. This alert encourages creditors to take extra steps to confirm your identity before completing a request for credit. One bureau will report the information to the other two, and your credit report will be mailed to you for review. The renewable fraud alert will be placed in your credit reports for one year.
- Contact Simplicity CU and any other financial institutions where you hold accounts, and immediately close all accounts that have been compromised
- Contact local law enforcement authorities and file an identity theft report
- Check with your local post office to see if any unauthorized change-of-address requests for you have been filed
- Visit the Federal Trade Commission’s Identity Theft website for more detailed information on how to recover from identity theft
